In today’s ever-evolving threat landscape, robust cybersecurity is not just an option – it’s a necessity. Organizations face increasingly sophisticated attacks, making it critical to have comprehensive visibility and rapid response capabilities. While often known for its search and analytics prowess, the Elastic Stack (formerly ELK Stack – Elasticsearch, Logstash, Kibana) has emerged as a formidable platform for security operations, offering a unified approach to threat detection, investigation, and response.
At Relipoint, we specialize in delivering cutting-edge observability and security solutions, helping our clients harness the full power of platforms like the Elastic Stack to protect their digital assets. In this post, we’ll dive deep into the Elastic Stack’s security capabilities and explain why it’s a game-changer for modern security teams.
Beyond Logs: The Elastic Stack as a Security Powerhouse
Traditionally, security teams relied on separate tools for log management, SIEM, endpoint protection, and threat intelligence. This often led to fragmented visibility, delayed detection, and inefficient workflows. The Elastic Stack breaks down these silos by providing a single, integrated platform for collecting, analyzing, and acting on security data from diverse sources.
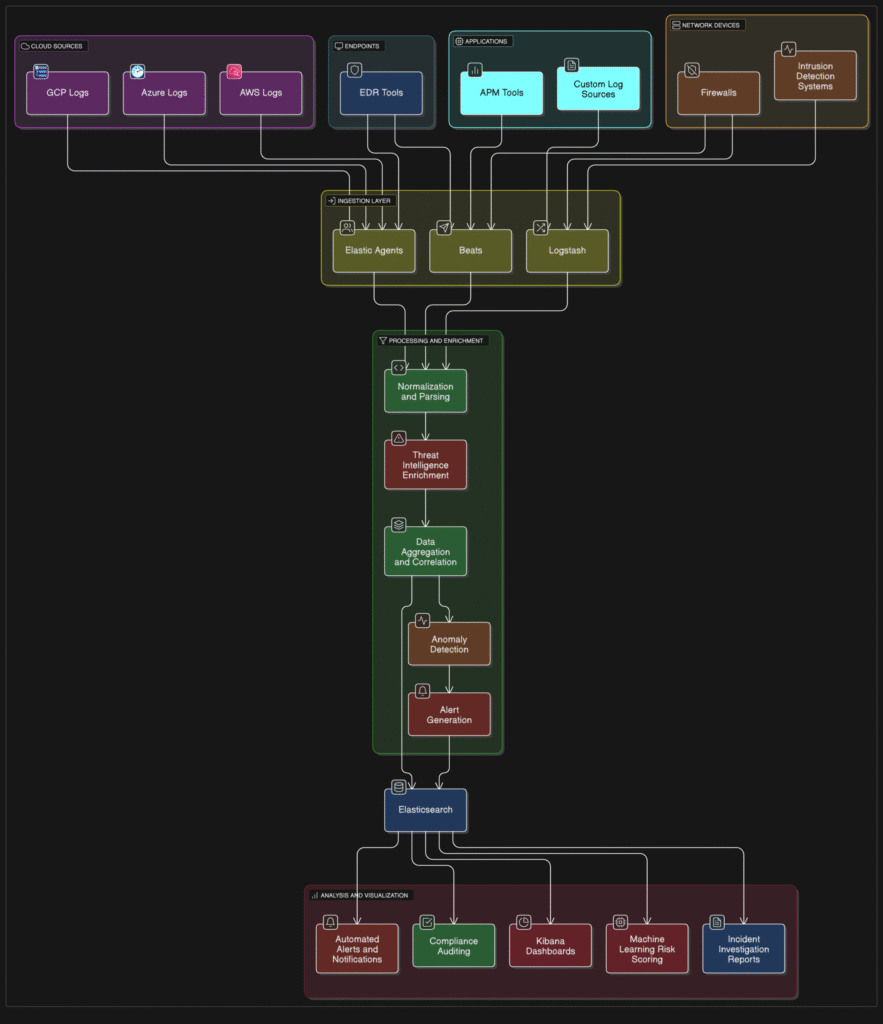
Elastic SIEM: Your Central Hub for Threat Detection
A cornerstone of the Elastic Stack’s security offering is Elastic SIEM. Built directly into Kibana, Elastic SIEM provides security analysts with a dedicated workspace to:
Gain Unified Visibility: Ingest and normalize security data from endpoints, network devices, cloud environments, and security tools using the Elastic Common Schema (ECS). ECS provides a consistent structure for disparate data, making analysis much easier.
Detect Threats with Speed: Utilize pre-built detection rules mapped to the MITRE ATT&CK® framework to identify common and advanced attack techniques. You can also create custom rules tailored to your specific environment.
Investigate Incidents Efficiently: Leverage interactive dashboards, timelines, and powerful search capabilities to quickly explore related events, understand the scope of an attack, and trace malicious activity.
Respond Decisively: Integrate with ticketing systems and orchestration tools to streamline incident response workflows and take swift action.

The tight integration of SIEM with the rest of the Elastic Stack means you can seamlessly pivot from a security alert to detailed log analysis, performance metrics, or user activity data, providing unparalleled context during investigations.
Endpoint Security: Protecting the Front Lines
Endpoints are often the initial point of compromise. Elastic Endpoint Security provides robust protection directly integrated with the Elastic Stack. Key features include:
Malware Prevention: Prevent known and unknown malware from executing on endpoints.
Exploit Prevention: Block common exploitation techniques used by attackers.
Behavioral Threat Protection: Identify malicious activity based on suspicious behavior patterns.
Visibility and Control: Gain deep visibility into endpoint activity and take response actions directly from Kibana.
By combining endpoint telemetry with network and log data in Elastic SIEM, security teams get a holistic view of potential threats originating from or targeting endpoints.
Advanced Threat Detection Capabilities
Beyond SIEM rules and Endpoint Security, the Elastic Stack offers several advanced capabilities to enhance threat detection:
Machine Learning for Anomaly Detection: Automatically identify unusual patterns in your security data that could indicate malicious activity, such as abnormal network traffic, unusual user logins, or suspicious process execution. This helps uncover threats that might evade traditional signature-based detection. Learn more about Elastic Machine Learning.
Threat Intelligence Integration: Enrich your security data with external threat intelligence feeds to identify known malicious IP addresses, domains, file hashes, and other indicators of compromise (IOCs).
User and Entity Behavior Analytics (UEBA): Analyze user and entity behavior over time to detect risky activities, insider threats, and compromised accounts.
Relipoint and Elastic: Your Partner in Cybersecurity
Implementing and optimizing a comprehensive security monitoring solution like the Elastic Stack requires expertise. At Relipoint, our team of certified professionals has extensive experience in designing, deploying, and managing Elastic Stack environments tailored to our clients’ specific security needs.
We help you:
Assess Your Security Requirements: Understand your unique threat landscape and data sources.
Design and Implement Your Elastic Security Solution: Configure Elastic SIEM, Endpoint Security, data ingestion pipelines, and detection rules.
Integrate with Existing Tools: Ensure seamless integration with your current security infrastructure.
Provide Ongoing Support and Optimization: Ensure your Elastic security deployment remains effective and up-to-date.
Develop Custom Dashboards and Reports: Create visualizations that provide actionable insights for your security team.
By partnering with Relipoint, you can unlock the full potential of the Elastic Stack’s security capabilities, strengthen your security posture, and improve your ability to detect, investigate, and respond to threats effectively.
Conclusion
The Elastic Stack is far more than just a logging and analytics platform; it’s a powerful, integrated security solution that provides the visibility, detection, and response capabilities necessary to defend against modern cyber threats. From its robust SIEM features and integrated Endpoint Security to advanced machine learning and threat intelligence, Elastic offers a comprehensive approach to cybersecurity.
Ready to enhance your security operations with the Elastic Stack? Contact Relipoint today to learn how we can help you build a resilient and effective security monitoring solution.
External Resources: